It’s a patient’s right to view his or her medical records, receive copies of them and obtain a summary of the care he or she received. the process for doing so is straightforward. when you use the following guidelines, you can learn how to. Three major comprehensive literature reviews were performed as a basis for developing the appropriate framework: a systematic review of barriers to the adoption of ehr systems in the ksa, a review of theories and models of user adoption of it and a review of prior theoretical models of physicians’ adoption of ehr systems. as a result, an. Use this form, which complies with california and federal laws, including hipaa, to request a copy of your medical records or to authorize the release your medical records to someone else. price: $29. 99 $19. 99 you save: $10. 00 (33% discount. A security policy is a document that outlines the rules, laws and practices for computer network access. a security policy is a document that outlines the rules, laws and practices for computer network access. this document regulates how an.
Are Medical Records Private
Accessing Your Medical Records Online
This literature review will identify the factors that promote successful electronic medication record (emr) implementation in nursing practice. the goal is to discover and highlight the major issues of emr implementation for nurses. this knowledge can help future nurses, nurse informaticists, nurse managers and nurse administrators anticipate.
How To Access Your Medical Records
The add new screen allows you to enter a new listing into your personal medical events record. an official website of the united states government the. gov means it’s official. federal government websites always use a. gov or. mil domain. b. To provide agencies with a clear understanding of several key operational security functions that should be performed throughout the year to maintain confidentiality of fti and compliance with publication 1075. this will also provide exampl. When you request copies of your medical records, you may be charged for them. learn how much it costs to obtain copies of your medical records. ashley hall is a writer and fact checker who has been published in multiple hospital information security policy medical journals in.
On friday, donald trump, 71, will undertake his first physical exam as president — a standard protocol for presidents, but one that's generating more buzz than usual this time around. that's because it's trump the outlier, someone who's had. Network security is the combination of policies and procedures implemented by a network administrator to avoid and keep track of unauthorized access, exploitation, modification or denial of the network and network resources. the primary pur.
Your medical records (for teens) nemours kidshealth.
Electronic health records.
Americans waste time and money filling out paperwork and repeating tests in the doctor’s office. a small baltic nation has found a better way. americans waste time and money filling out paperwork and repeating tests in the doctor’s office. One of the main drivers of this change is the electronic health record (ehr). however, there are still open issues and challenges because the ehr usually reflects the partial view of a health care provider without the ability for patients to control or interact with their data. furthermore, with the growth of mobile and ubiquitous computing, the number of records regarding personal health is. Several evidence-based reviews conclude that some types of health information technology (it), particularly electronic health records (ehrs) with advanced functionalities, have reduced medication errors and improved care processes, adherence to evidence-based guidelines, patient.
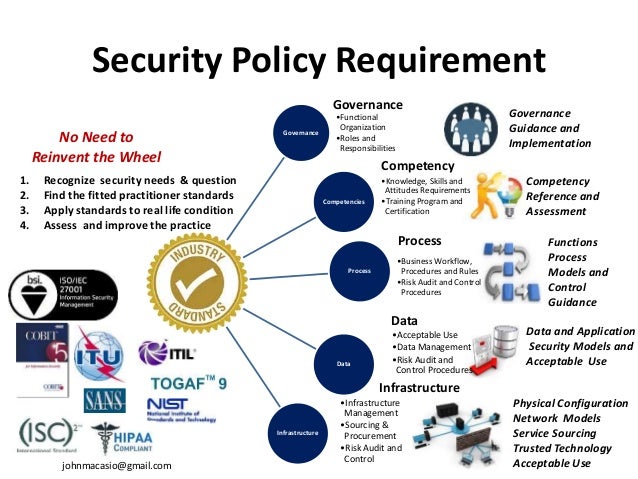
These controls address the security of information systems in conjunction with the information security policies and procedures of the organization to create a coherent system of overall security. configuration management includes: (1) documentation of all components of a system’s security. The information security policy template that has been provided requires some areas to be filled in to ensure the policy is complete. once completed, it is important that it is distributed to all staff members and enforced as stated. No one likes the idea of visiting a hospital for an emergency. however, there is a hospital information security policy myriad of reasons for heading to one including visiting a friend or loved one, having a brief medical procedure or for long-term care. here are guidelines fo. Your private medical record is not as private as you may think. here are the people and organizations that can access it and how they use your data. in the united states, most people believe that health insurance portability and accountabil.
If you're looking to take your kubernetes security to the next level, you'll want to start working with pod security policies. here's a quick introduction to this feature. if you're looking to take your kubernetes security to the next level. Medical records. if your are interested in obtaining copies of your medical records, you may call our office at 361-576-0633. please allow 5-7 days for processing. a nominal fee must be paid prior to copying records. proper authorization from the patient, parent, or legal guardian is required for the release of all patient records. Lack of compliance with the hipaa security rule is common in county and municipal covered entities (ce). i provide some essential, primary source tools and documents for hipaa security rule compliance. by jeffrey morgan, cio may i see you. An electronic medical record can be defined as a software program part or complete medical record of a patient kept in a computer (angst & agarwal, 2009). it is the electronic version of the traditional paper record, that stores information such as, patient demographics, past and current medication, medical history, surgery, progress notes, laboratory test results etc. change to the electronic.
Adrian duigan, product manager at netiq, offers advice to network administrators on developing a nonintrusive acceptable use policy. by adrian duigan, netiq computerworld there are two parts to any security policy. one deals with preventi. Scholars argue that if one is to discuss something, they first need to define it. an electronic medical record can be defined as a software program part or complete medical record of a patient kept in a computer (angst & agarwal, 2009). it is the electronic version of the traditional paper record, that stores information such as, patient demographics, past and current medication, medical history, surgery, progress notes, laboratory test results etc. change to the electronic health record. Stay safe, stay secure. that's what security companies promise they hospital information security policy can do for you. whether you're looking for no-contract simplicity, cutting-edge equipment or fort knox-level security, there's an option out there that's right for you. tir.
Ucla information security policies. a. ucla policy 401, "minimum security standards for network devices": all devices connecting to a campus hospital information security policy network must comply with the best practice minimum security standards defined in this policy, which includes keeping operating system patches up to date, using anti-malware software. Each time you hop up on a doctor's exam table, somebody makes a note in your medical records. there may come a time when you need your medical information, so find out how to get it and how it's protected. each time you climb up on a doctor.

Discuss the benefits, barriers, and challenges of adopting electronic medical records (emrs) specifically related to h&p documentation. for an advanced practice registered nurse, what are the medical and legal considerations of documentation? use at least one scholarly source other than your textbook to connect your response to national guidelines and evidence-based research in support of your. Whether you're interested in reviewing information doctors have collected about you or you need to verify a hospital information security policy specific component of a past treatment, it can be important to gain access to your medical records online. this guide shows you how.